XML External Entity (XXE) Attacks
What are XML External Entity (XXE) Attacks?
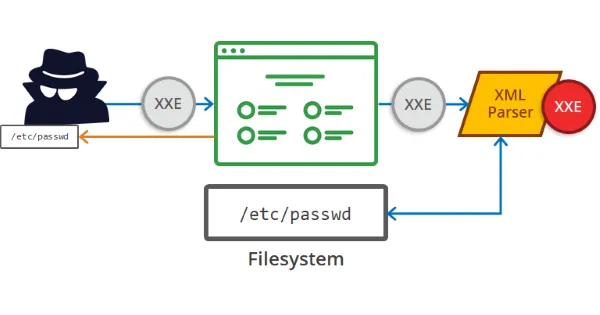
XML External Entity (XXE) attacks are a type of security vulnerability that occurs when an application processes XML input from untrusted sources without proper validation. Attackers can exploit XXE vulnerabilities to disclose internal files, perform remote code execution, or launch denial-of-service attacks.
Example of an XXE Attack
Consider an XML parsing function that processes user-submitted XML data:
<?xml version="1.0" encoding="UTF-8"?>
<order>
<customer>John</customer>
<product>Widget</product>
</order>
An attacker could craft a malicious XML input like this:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE evil [
<!ELEMENT evil ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >
]>
<order>
<customer>John</customer>
<product>&xxe;</product>
</order>
In this example, the attacker references an external entity that fetches sensitive system information (the /etc/passwd file) and includes it in the XML response.
Prevention Measures
To prevent XXE attacks, consider implementing these security measures:
- Input Validation: Validate and sanitize XML inputs to ensure they conform to expected structures.
- Disable External Entity Processing: Disable the processing of external entities in XML parsers.
- Use Safe Parsers: Utilize secure XML parsers that prevent XXE vulnerabilities.
- Least Privilege: Restrict file system access for application processes to limit potential damage.