What is DirBuster?
DirBuster is a multi-threaded java application designed to brute force directories and files names on web/application servers. It is often used during penetration testing to discover resources that are not linked from the public application.
DT using DirBuster
DirBuster can be used to perform directory traversal attacks by brute forcing directories and file names on web/application servers. It comes with a total of 9 different lists; this makes DirBuster extremely effective at finding those hidden files and directories. And if that was not enough, you can also use your own custom lists to cover any web application.
DirBuster Example
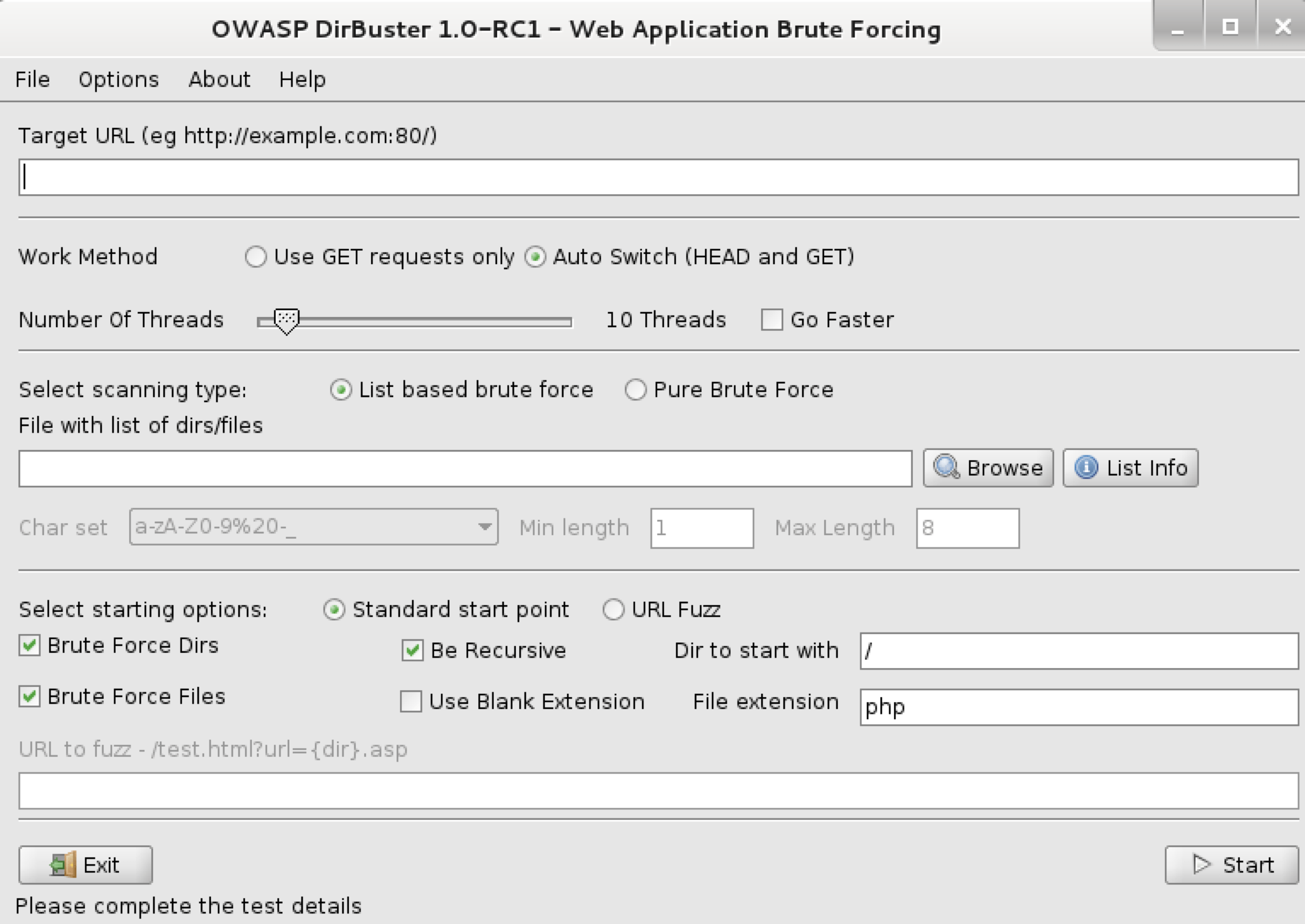
Here is a simple example of how to use DirBuster:
// Start DirBuster
java -jar DirBuster-1.0-RC1.jar
// Set the target URL
Target URL: http://target.com/
// Set the list for brute forcing
List: directory-list-2.3-medium.txt
// Start the attack
Start
Prevention
Preventing directory traversal attacks involves proper input validation and sanitization. This includes:
- Input validation: Validate user input by only accepting expected values.
- Use allow lists: Only allow known good input to pass through.
- Sanitize input: Remove or replace special characters from user input.
- Use chroot jails: Limit the user's environment to a specific directory tree.