
What is a Computer Network?
A computer network is a group of interconnected computers that communicate with each other to share resources and information. These networks can range in size from small, such as a home network connecting a few devices, to vast, like the internet, which connects billions of computers worldwide. The primary purpose of a computer network is to facilitate communication, enable data sharing and resource pooling, and provide a cost-effective way to access remote databases and applications.
Types of Computer Networks
Computer networks can be categorized based on their geographical coverage, the distribution of resources, and their size. Here are the most common types:
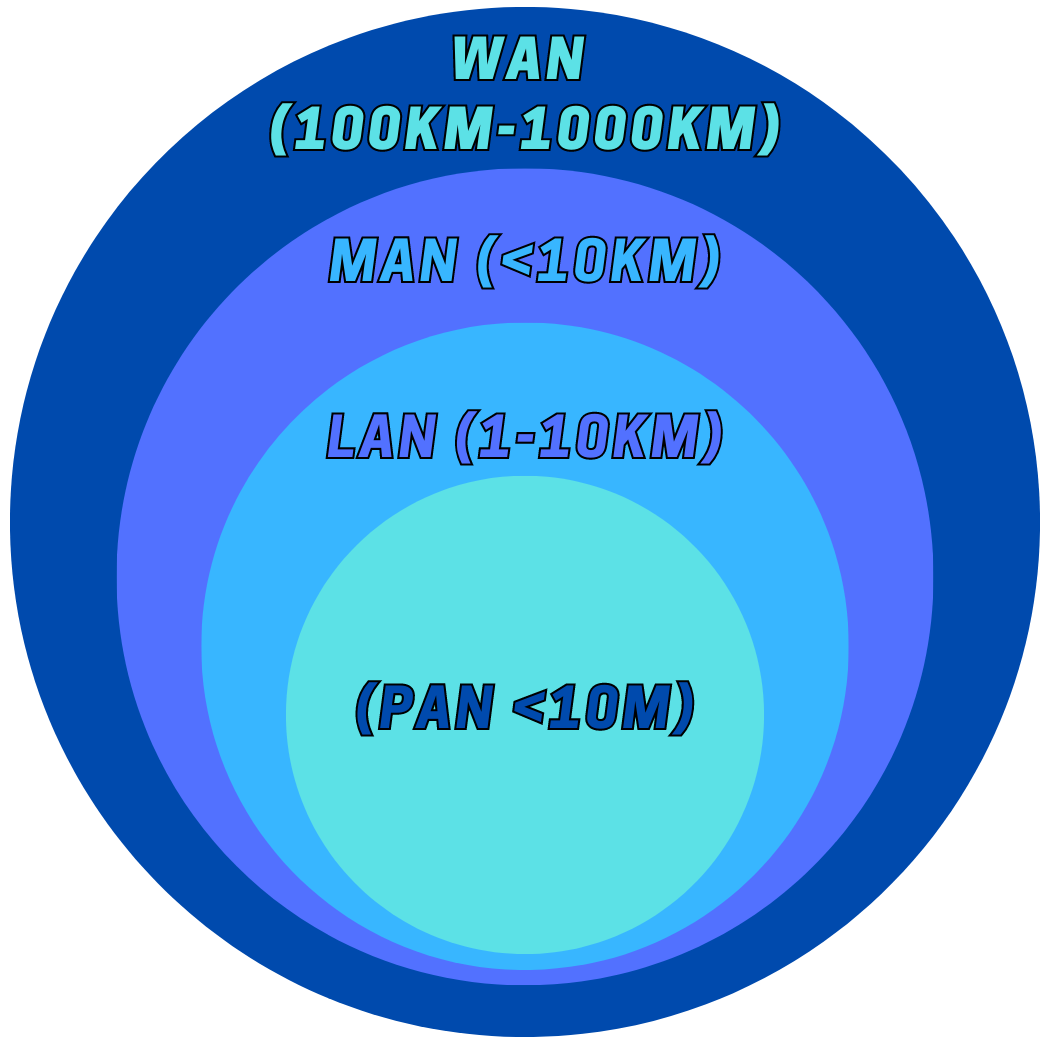
- Local Area Network (LAN) - A LAN connects computers in a small area, such as a home, office, or school. LANs are known for their high data transfer rates and relatively small geographical coverage. They are typically owned, controlled, and managed by a single person or organization.
- Wide Area Network (WAN) - A WAN covers a large geographical area, often spanning cities, states, or even countries. The internet is the largest WAN, connecting computers worldwide. WANs use technologies like MPLS, ATM, Frame Relay, and X.25 for connectivity over the longer distances.
- Metropolitan Area Network (MAN) - A MAN is larger than a LAN but smaller than a WAN. It connects computers in a city or large campus. MANs are often used for providing internet connectivity in cities or as a network for a large corporate office.
- Personal Area Network (PAN) - A PAN is a network for devices used by a single person, often connected via Bluetooth or Wi-Fi. These networks typically span a few meters and can connect devices like a computer, smartphone, printer, and tablet.
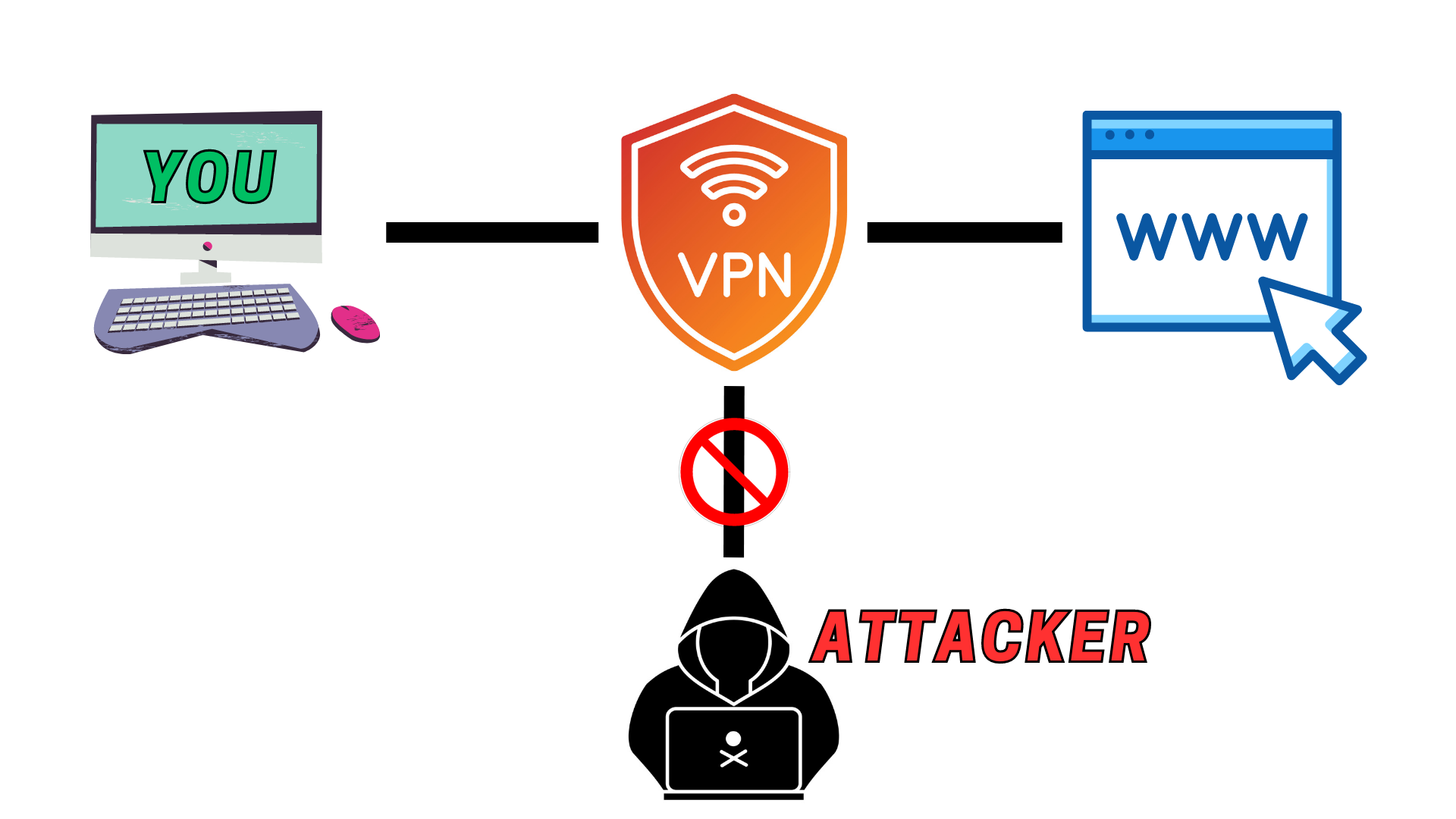
- Virtual Private Network (VPN) - A VPN uses the internet to provide remote offices or individual users with secure access to their organization's network. VPNs encrypt connections to ensure security and privacy.
Network Topologies
Network topology refers to the arrangement of different elements (links, nodes, etc.) in a computer network. It defines how devices or nodes in a network are connected and how they communicate with each other. Here are the primary types:
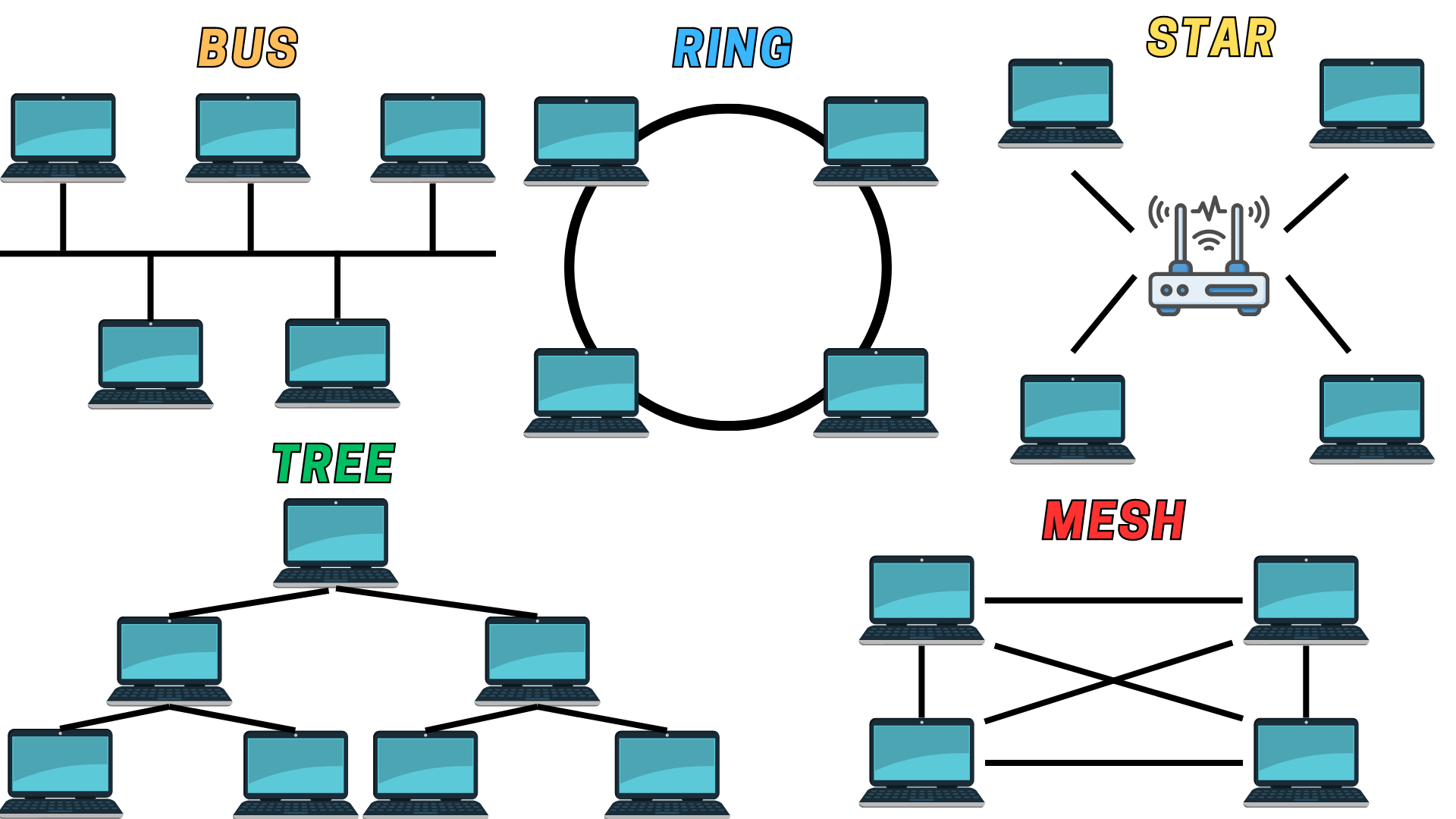
- Bus Topology - In a bus topology, all devices are connected to a single central cable, the bus. Data from the source computer travels in both directions to all machines until it finds the intended recipient. While easy to connect, a break in the main cable can stop all transmission.
- Ring Topology - In a ring topology, each device is connected to two other devices, forming a ring for signals to travel. Each computer is a point on the ring and can send messages in one direction. A failure in any cable or device breaks the loop and can take down the entire network.
- Star Topology - In a star topology, all devices are connected to a central hub. The hub acts as a repeater for data flow. This topology is easy to manage and expand, but if the hub fails, the whole network goes down.
- Tree Topology - A tree topology is a combination of star and bus topologies. It has a central root node (the top level of the hierarchy) that connects to one or more other nodes that are one level lower in the hierarchy.
- Mesh Topology - In a mesh topology, devices are interconnected, with multiple paths between any two nodes. This topology provides high redundancy. If one cable or node fails, there are many other ways for data to reach its destination.
Network Protocols
Network protocols are a set of rules or procedures for transmitting data between electronic devices, such as computers. In the context of data communication, a protocol is a defined set of rules for data transfer which the connected devices follow. Here are some key protocols:
- Transmission Control Protocol (TCP) - TCP is one of the main protocols in the Internet protocol suite. It is a transport protocol that's used to send data over the network in a reliable and error-checked stream. It ensures data is delivered correctly by checking for errors and ensuring that data arrives in the correct sequence.
- Internet Protocol (IP) - IP is responsible for sending and routing packets of data from the source to the destination. IP addresses are a key part of how the internet works, allowing for the unique identification of devices on a network.
- HyperText Transfer Protocol (HTTP) - HTTP is used for transmitting hypertext over the internet. HTTP defines how messages are formatted and transmitted and what actions web servers and browsers should take in response to various commands.
- File Transfer Protocol (FTP) - FTP is used for transferring files between computers on a network. It allows users to access files on the server and also upload files to the server.
- Simple Mail Transfer Protocol (SMTP) - SMTP is used for sending emails. It's a protocol for sending email messages between servers. Most email systems use SMTP to send messages from one server to another.
Network Security
Network security is a critical aspect of managing networks. It involves implementing measures to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources.
Common Network Threats
- Malware - Malicious software such as viruses, worms, and ransomware can infect a network and cause significant damage. Malware can delete files, steal sensitive information, or even take control of a machine.
- Phishing - Phishing is a method of stealing sensitive information by pretending to be a trustworthy entity. Phishing attacks often come in the form of deceptive emails or websites that trick users into revealing their personal details.
- Denial of Service (DoS) Attacks - In a DoS attack, attackers overload a network or website with traffic, making it unavailable to users. This can be done by flooding the network with more data than it can handle or exploiting weaknesses in the network's protocols.
- Man-in-the-Middle (MitM) Attacks - In a MitM attack, the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other.
Network Security Measures
- Firewalls - Firewalls are security systems that monitor and control incoming and outgoing network traffic based on predetermined security rules. They establish a barrier between a trusted internal network and untrusted external networks.
- Antivirus Software - Antivirus software is designed to detect, prevent, and remove malware. It can protect against viruses, spyware, adware, and other types of malicious software.
- Virtual Private Networks (VPNs) - VPNs can provide secure and encrypted connections, which offer greater privacy and security online. They can protect data from being intercepted and keep internet activities private.
- Regular Updates - Keeping all systems and software updated is crucial as updates often include patches for security vulnerabilities. Regular updates can protect against many common threats.
Packet Tracer
Packet Tracer is a powerful network simulation program that allows students to experiment with network behavior and ask "what if" questions. It provides an intuitive, graphical environment for network design and enables users to see how packets move in a network. Packet Tracer's multiuser functionality also allows students to collaborate and compete with each other in a shared network environment. Packet Tracer is particularly useful for understanding how data travels in a network and how devices communicate with each other. It allows users to simulate the configuration of Cisco routers and switches. By using Packet Tracer, students can design, configure, and troubleshoot networks using virtual equipment. For those studying for CCNA Certification, it is an invaluable tool for gaining practical network understanding.