
DoS using LOIC (Low Orbit Ion Cannon)
The Low Orbit Ion Cannon (LOIC) is an open-source network stress testing and DoS attack application. Originally developed by Praetox Technologies, it has become one of the most popular tools for conducting DoS attacks, primarily due to its simplicity and user-friendly interface. However, it's essential to note that using LOIC for malicious purposes is illegal and unethical. This guide is for educational purposes only.
Installation of LOIC
LOIC can be installed on both Windows and Linux platforms. Below are the installation guides for each:
Windows Installation
- Visit the official LOIC page on SourceForge.
- Click on the "Download" button to start downloading the .exe file.
- Once downloaded, extract the zip file and locate the .exe file and double-click to run it.
- Follow the on-screen instructions to complete the installation.
Linux Installation
For Linux, LOIC is typically run using the Mono framework:
- First, install Mono by running the following command:
sudo apt-get install mono-complete
- Download the LOIC tool from the sourceforge link
- Extract the downloaded file to a preferred directory.
- Navigate to the directory and run LOIC using the command:
mono LOIC.exe
Using LOIC for DoS
Once LOIC is installed, you can use it to perform a DoS attack. Here's a step-by-step guide:
- Open LOIC by double-clicking its icon (Windows) or using the mono command (Linux).
- In the "URL" or "IP" field, enter the target's IP address or domain name.
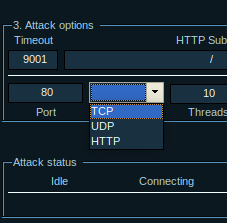
- Choose the method of attack. The most common method is TCP.
Set the port number. If you're unsure, the default HTTP port is 80. - Adjust the thread count. A higher number will send more requests to the target.
- Click on the "IMMA CHARGIN MAH LAZER" button to start the attack.
- Monitor the attack using the logs and status provided in the LOIC interface.
- To stop the attack, click on the "Stop Flooding" button.
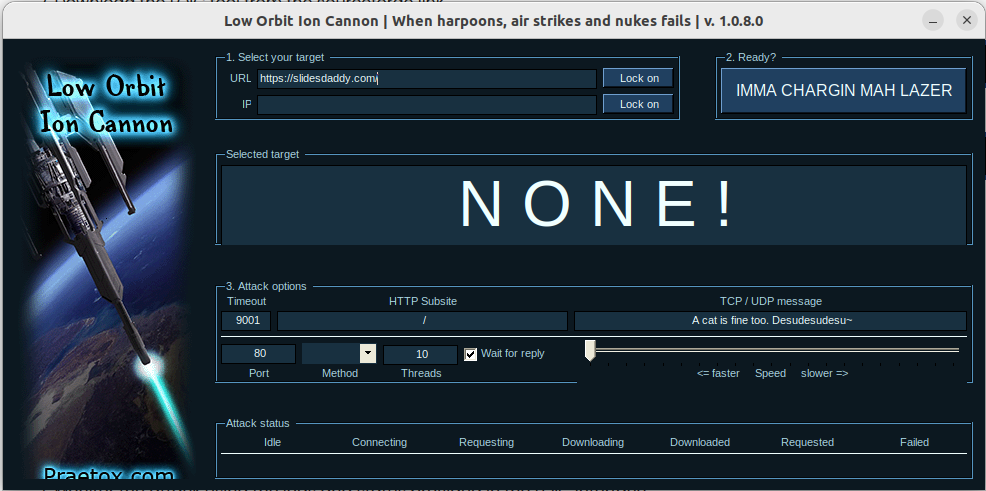
Note that I own the domain slidesdaddy.com, so I am legally testing this.

Conclusion
While LOIC is a powerful tool for stress testing and understanding DoS attacks, it's crucial to use it responsibly and ethically. Launching unauthorized attacks can lead to severe legal consequences. Always ensure you have permission before testing any network or system.