What is Wireshark?
Wireshark is an open-source tool that allows users to analyze network traffic in real-time. It supports various network protocols and can be used on multiple operating systems, including Windows, macOS, and Linux.
Wireshark is the most widely-used network protocol analyzer that lets you capture and interactively browse the traffic running on a computer network. It provides the ability to drill down and read the contents of each packet, making it a valuable tool for network professionals and ethical hackers. This guide will walk you through the essential aspects of using Wireshark for network analysis, focusing on its applications in cybersecurity.
1.1 Key Features:
- Packet Capture and Analysis: Capture live packet data from a network.
- Protocol Inspection: Detailed analysis of various protocols.
- Filtering: Apply filters to focus on specific traffic.
- Graphical Interface: User-friendly GUI for ease of use.
- Exporting Data: Export data in various formats for further analysis.
Installing Wireshark
Before diving into network analysis, you'll need to install Wireshark on your system. Follow the instructions specific to your operating system from the official Wireshark website.
Capturing Packets with Wireshark
3.1 Selecting an Interface:
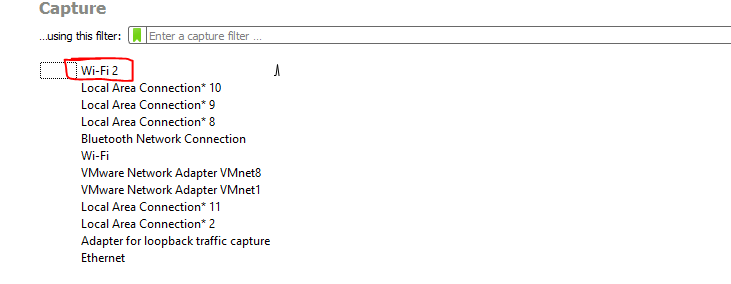
Open Wireshark. Select the network interface you want to monitor. Click on the 'Start' button to begin capturing packets.
3.2 Applying Filters:
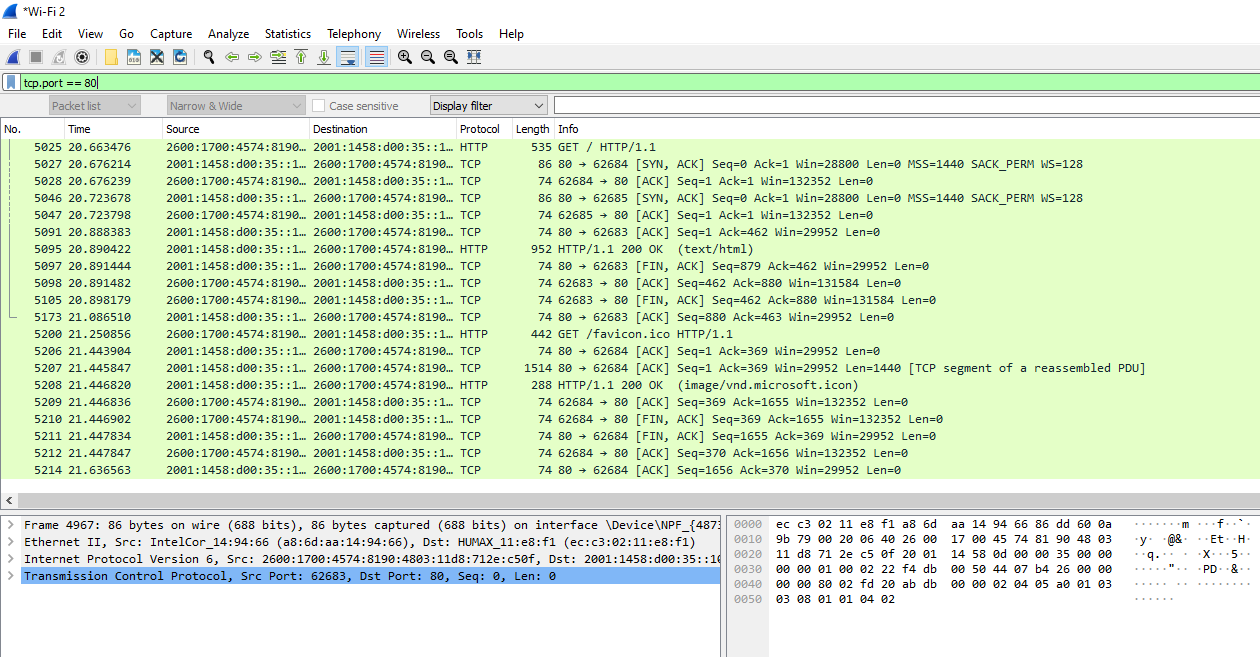
Use display filters to narrow down specific traffic. Example: tcp.port == 80 to filter HTTP traffic.
Analyzing Network Traffic
4.1 Understanding Protocols:
Analyze different protocols like TCP, UDP, HTTP, etc. Inspect individual packets for detailed information. Wireshark provides color-coded protocols, allowing for quick identification and analysis. Understanding the structure of these protocols is essential for identifying potential security threats and ensuring proper network functionality.
4.2 Detecting Anomalies:
Identify unusual patterns that may indicate malicious activity. Analyze failed connection attempts, unusual ports, etc. Wireshark's statistical tools can help in spotting trends and patterns that might signify an attack or a compromised system. Regular monitoring and analysis can prevent potential breaches and ensure network integrity.
Wireshark in Cybersecurity
5.1 Identifying Vulnerabilities:
Analyze network to find weak points and vulnerabilities. Assist in penetration testing. Wireshark can be used to simulate attacks in a controlled environment, helping to identify weak spots in security measures. By understanding these vulnerabilities, security professionals can take proactive steps to strengthen defenses and reduce risks.
5.2 Investigating Incidents:
Use Wireshark to investigate security incidents. Analyze logs to trace back malicious activities. In the event of a security breach, Wireshark's detailed logs can be invaluable in tracing the origin and nature of the attack. This information can be used to prevent future incidents and to provide evidence if legal action is necessary.
Best Practices and Ethical Considerations
Always Seek Permission: Only analyze networks you are authorized to access. Unauthorized access can lead to legal consequences. Protect Sensitive Data: Be mindful of personal and sensitive information. Ensure that captured data is stored securely and that privacy is maintained. Stay Updated: Regularly update Wireshark to ensure you have the latest security patches. Outdated software may contain vulnerabilities that can be exploited. Misuse of Wireshark can lead to legal and professional repercussions.
Resources to Learn Wireshark
Wireshark Official DocumentationWireshark Tutorial in 10 minutes