IP Spoofing
IP spoofing is a technique where an attacker alters the source IP address in a packet's header to masquerade as a trusted host and gain unauthorized access to a system or to launch a reflected DDoS attack. This method can be used to bypass IP-based security measures, deceive network devices, or mislead intrusion detection/prevention systems.
Understanding IP Spoofing
Every packet transmitted over the Internet contains a source and destination IP address. In IP spoofing, the attacker modifies the source IP address to hide their identity or impersonate another system. This can be particularly dangerous because many authentication methods and services rely on IP addresses to establish trust.
How IP Spoofing Works
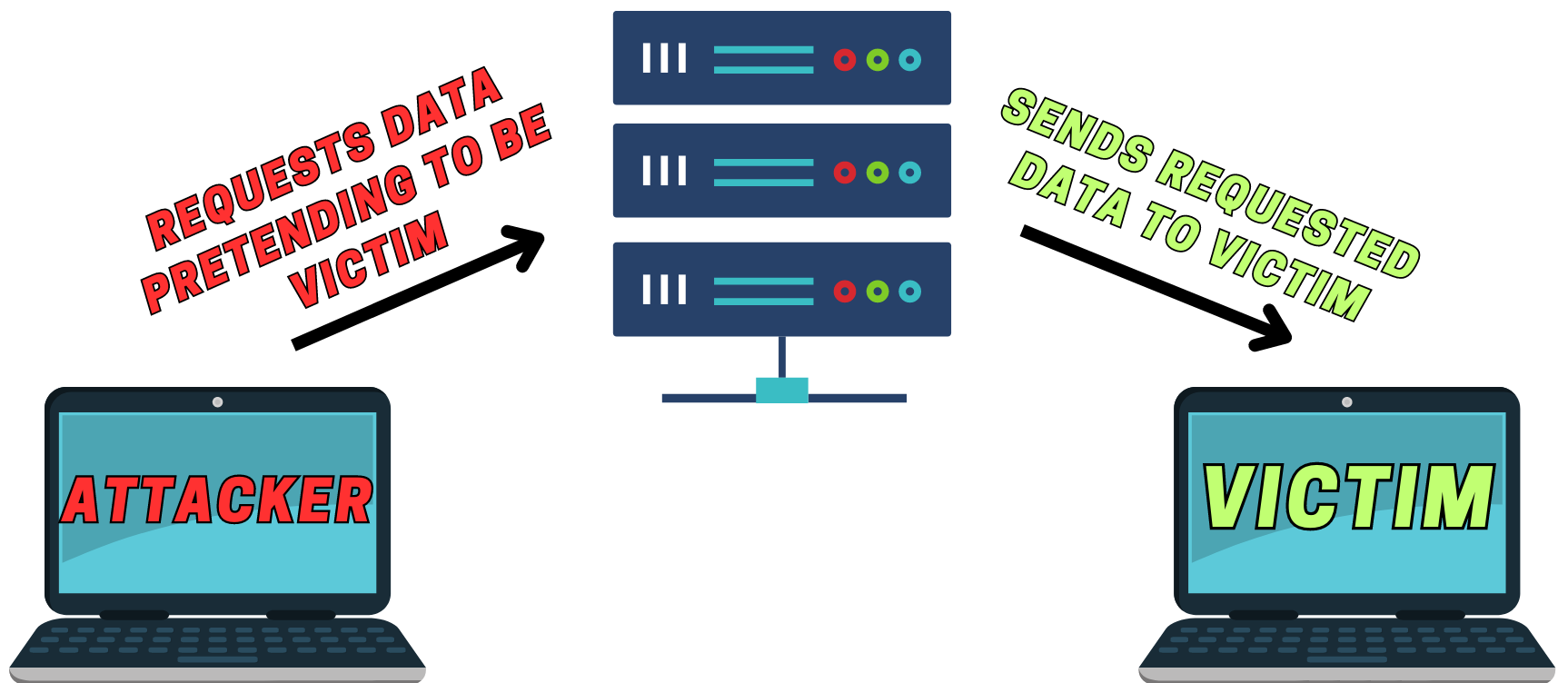
IP spoofing is typically used in conjunction with another attack method, such as a DDoS attack or man-in-the-middle attack. The attacker sends multiple packets with a falsified source IP address to a target system. The target system, believing the source to be legitimate, may:
- Accept malicious data from the attacker.
- Be used as a reflector in a DDoS attack against another target.
- Provide the attacker with access to restricted resources.
Dangers of IP Spoofing
IP spoofing poses several threats, including:
- Unauthorized Access: Attackers can bypass IP-based authentication and gain unauthorized access to systems.
- Man-in-the-Middle Attacks: Attackers can intercept and modify communication between two parties without their knowledge.
- DDoS Attacks: By spoofing the source IP, attackers can direct the response to a third-party target, overwhelming it with traffic.
- Session Hijacking: Attackers can take over an existing user session by spoofing the user's IP address.
Prevention Measures
To protect against IP spoofing, consider the following measures:
- Implement ingress and egress filtering on network devices to block packets with spoofed source IP addresses.
- Use modern routing protocols that have built-in authentication mechanisms.
- Deploy intrusion detection and prevention systems to monitor and block suspicious activities.
- Use encrypted protocols like HTTPS and VPNs to ensure data integrity and authenticity.
Conclusion
IP spoofing is a significant threat in the realm of cybersecurity. By understanding its mechanisms and potential dangers, individuals and organizations can better prepare and defend against such attacks. Always ensure that you have the necessary permissions before conducting any IP spoofing tests for ethical purposes. Ethical hacking aims to improve security, not exploit it.