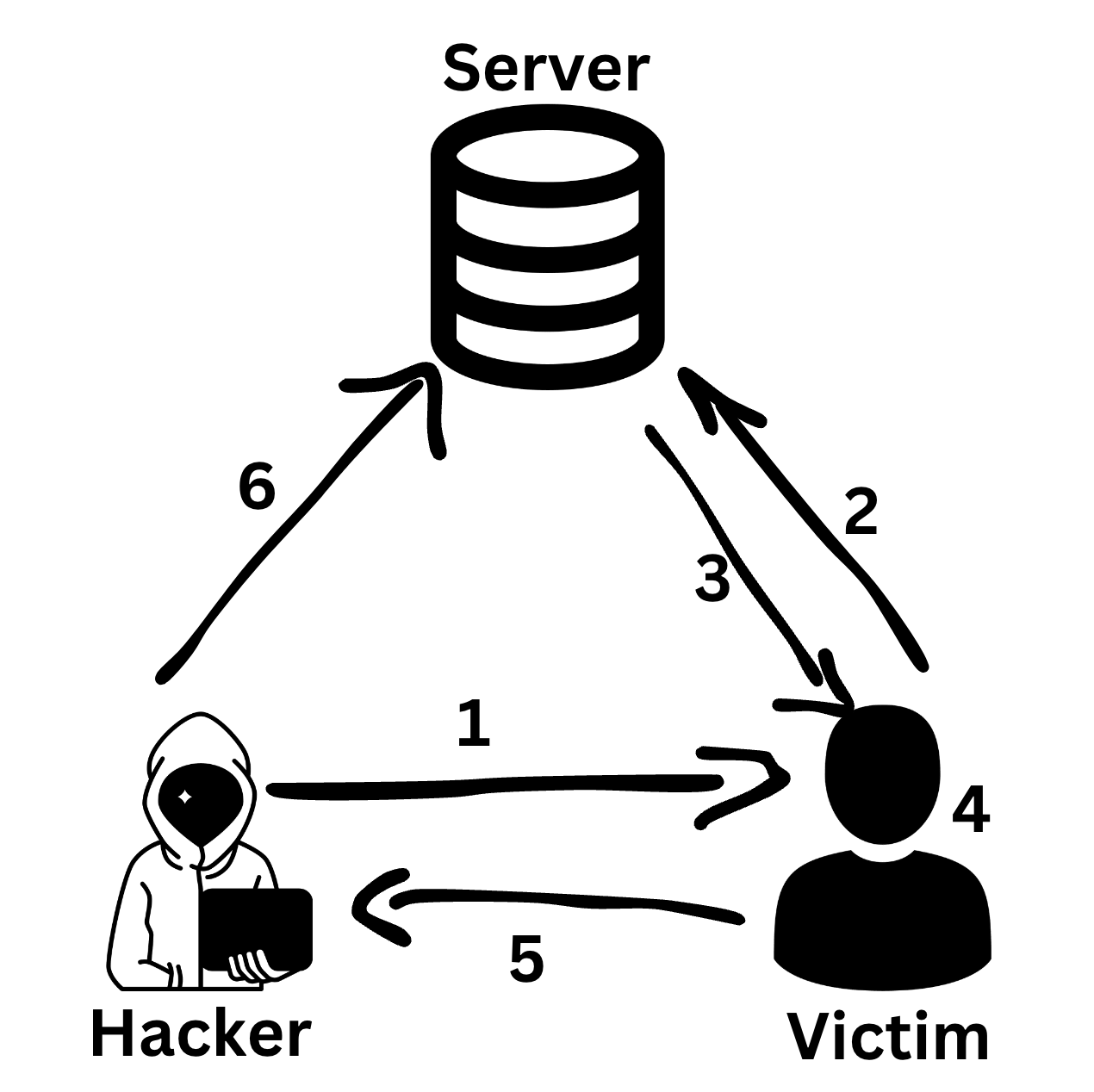
What is CSRF
Cross-Site Request Forgery (CSRF) is an attack that tricks the victim into submitting a malicious request. It uses the identity and privileges of the victim to perform an undesired function on their behalf. For most sites, browser requests automatically include any credentials associated with the site, such as the user's session cookie, IP address, etc. Therefore, if the user is authenticated to the site, the site cannot distinguish between legitimate requests and forged requests.
CSRF Attack Techniques
There are several techniques that attackers use to exploit CSRF vulnerabilities:
- Forced Browsing: This technique involves guessing the URL of certain server-side operations and forcing the victim's browser to perform those operations by using image tags, XSS, or other techniques to inject HTTP requests into the victim's browser.
- Session Riding: This technique involves performing actions on the victim's behalf by using the session cookie that the web application has issued to the victim.
- Cookie Injection: This technique involves injecting a cookie into the victim's browser, which is then used to authenticate a forged request.
Preventing CSRF
Preventing CSRF involves using anti-CSRF tokens, checking the HTTP Referer header, and using the SameSite cookie attribute. Anti-CSRF tokens can be included in requests and verified by the server. They must be unpredictable and securely generated. The HTTP Referer header can be checked by the server to see if the request is made from an authorized page. The SameSite cookie attribute can be used to disable third-party usage for a particular cookie, helping protect against CSRF attacks.