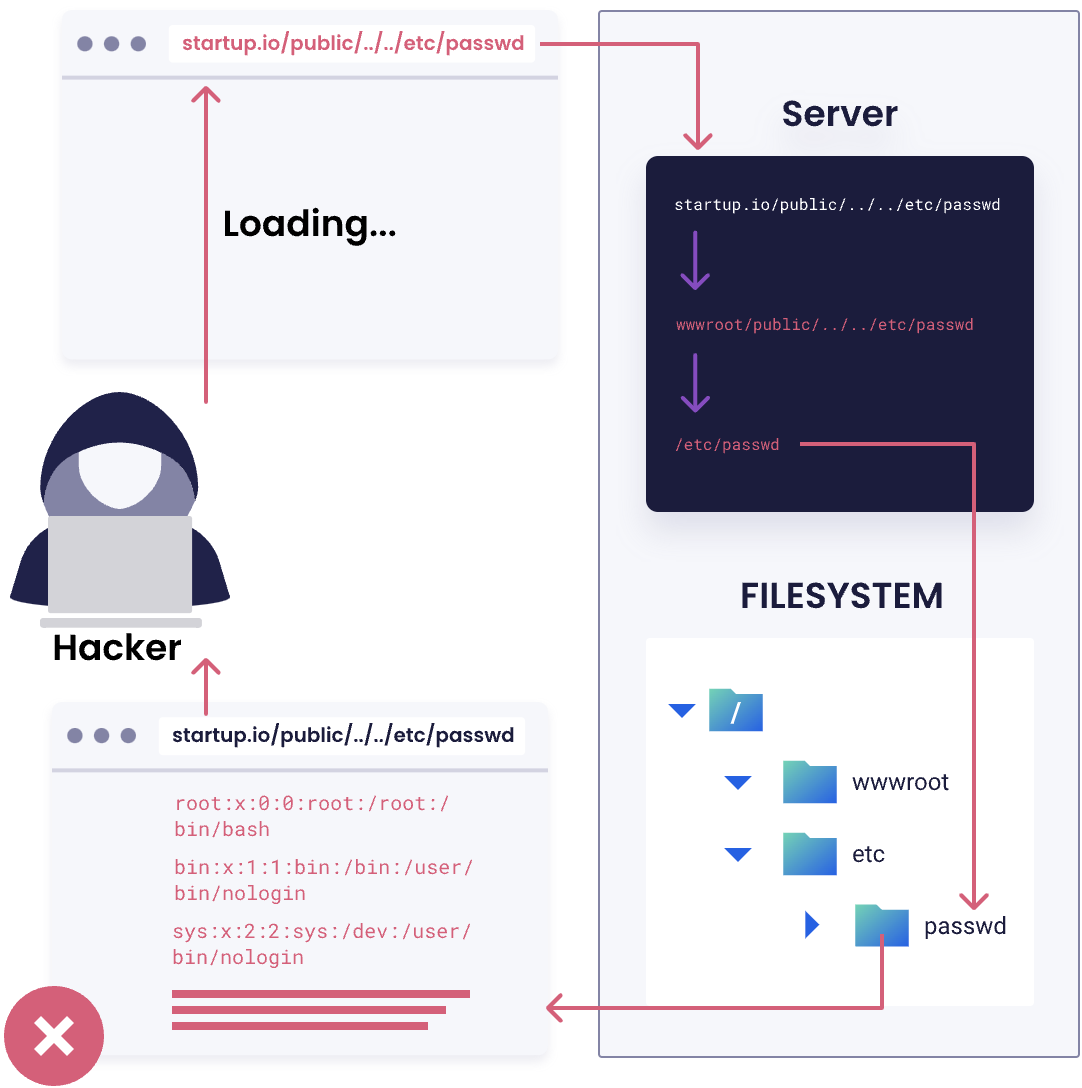
What is Manual Directory Traversal?
Manual directory traversal involves manipulating variables that reference files with “dot-dot-slash (../)” sequences and its variations or by using absolute file paths, it may be possible to access arbitrary files and directories stored on file system. This can be done by manually modifying the URL or by using tools such as Burp Suite to intercept and modify requests. This type of attack can lead to information disclosure, privilege escalation, or even remote code execution if files with sensitive data or functionality are accessed.
Manual Directory Traversal Example
Here is a simple example of a manual directory traversal attack:
// Original URL
http://example.com/view?file=example.txt
// Modified URL
http://example.com/view?file=../etc/passwd
In this example, the attacker modifies the "file" parameter in the URL to reference the "/etc/passwd" file, which is a sensitive file on Unix systems.
Prevention
Preventing manual directory traversal attacks involves proper input validation and sanitization. This includes:
- Input validation: Validate user input by only accepting expected values.
- Use allow lists: Only allow known good input to pass through.
- Sanitize input: Remove or replace special characters from user input.
- Use chroot jails: Limit the user's environment to a specific directory tree.