
File Inclusion with Burp Suite
File Inclusion vulnerabilities, particularly Remote File Inclusion (RFI), can pose significant security risks to web applications. RFI allows attackers to include files from external sources, potentially leading to code execution on the server. Burp Suite offers tools to identify and exploit such vulnerabilities effectively.
Understanding Remote File Inclusion (RFI)
RFI is an attack vector that targets the inclusion of files from external domains. The vulnerability arises when user input is used to fetch a file without adequate validation, allowing an attacker to supply external URLs. This can lead to malicious scripts being executed on the server or data theft.
Getting Ready
For this demonstration, we'll use the OWASP Mutillidae II application to identify potential RFI vulnerabilities. Ensure that both Burp Suite and the OWASP BWA VM are operational. Also, configure Burp Suite with your browser to intercept and analyze web traffic.
Step 1: Navigate to Target Application
Access the web application you want to use. For this demonstration, I am using the OWASP Multillidae II, which you can download here. Once on the application, navigate to the login screen and click on the "Login" option from the top menu.
Step 2: Capture the Request
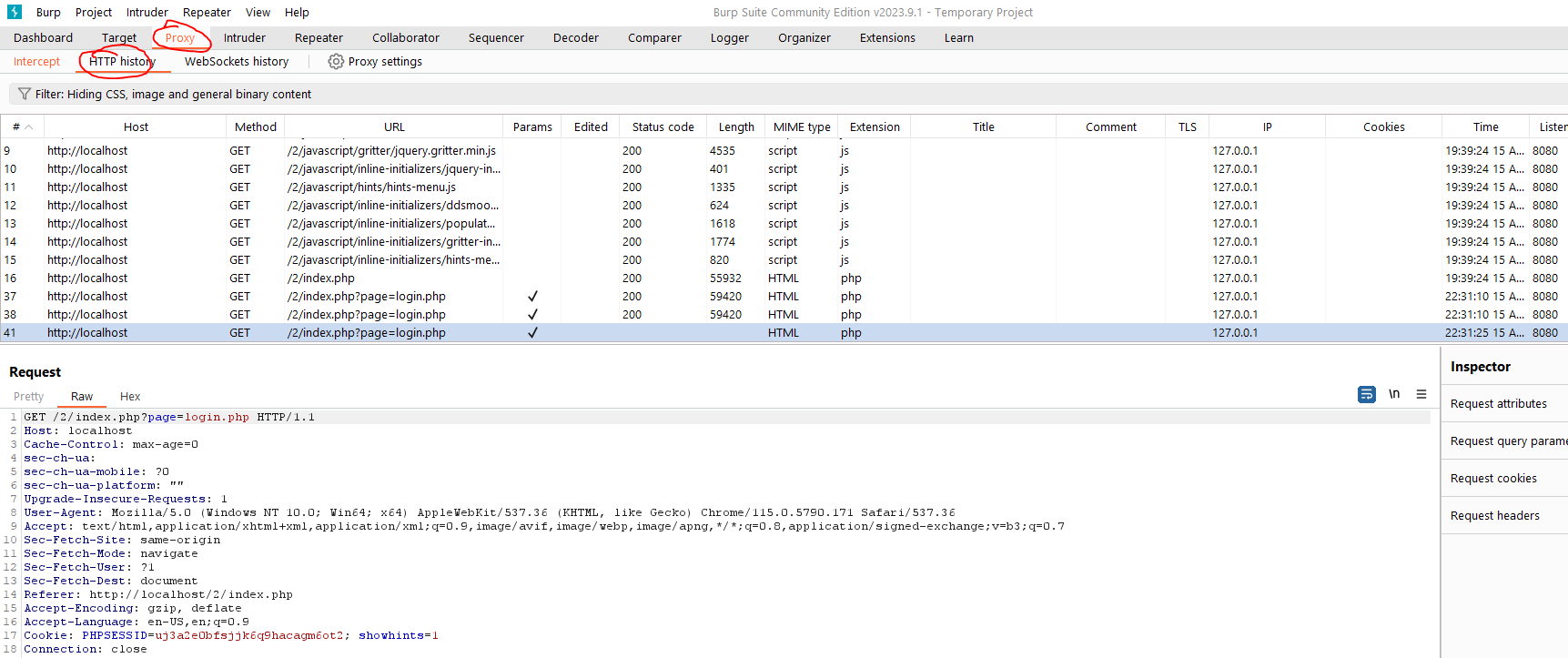
Within Burp Suite, turn "Intercept is on", and locate the request you just made in the Proxy | HTTP history table. Specifically, look for the call directed to the `login.php` page. Take note of the `page` parameter, as this will be crucial for our test.
Step 3: Intercept and Modify the Request
Switch to the Proxy | Intercept tab in Burp Suite and activate the interception. Now, reload the login page in your browser. The request will be halted in the Proxy | Intercept tab. Here, you'll modify the value of the `page` parameter. Replace its current value with an external URL, for instance, the login page of another application on the OWASP BWA VM. Remember, in a real-world scenario, this URL would be under the attacker's control.

The directory "1" is another example web application
Step 4: Observe the Result
Click the "Forward" button. After forwarding the modified request, deactivate the interception in Burp Suite. Return to your browser and observe the loaded page. If the external page is displayed within the context of the Mutillidae application, it indicates a potential RFI vulnerability.
How It Works
The underlying issue here is the lack of proper data validation for the `page` parameter. Without ensuring that provided values are restricted to a predefined list, attackers can exploit this weakness to include files from external sources.
Additional Resources
For a more in-depth understanding and advanced techniques, refer to this simple File Inclusion Tutorial.