What is Malware?
Malware, short for malicious software, refers to any program or code designed to harm a computer, network, or server. It includes various harmful software types like ransomware, keyloggers, trojans, worms, and viruses. Malware attacks often start through phishing, social engineering, or corrupt downloads, aiming to control the system and communicate sensitive data back to the attacker. The attack's outcome can range from system disruption to demanding ransom for system restoration.
Malware comes in many forms, most popularly as a virus, worm, or trojan. Other forms of popular malware include ransomware, spyware, keyloggers, etc.
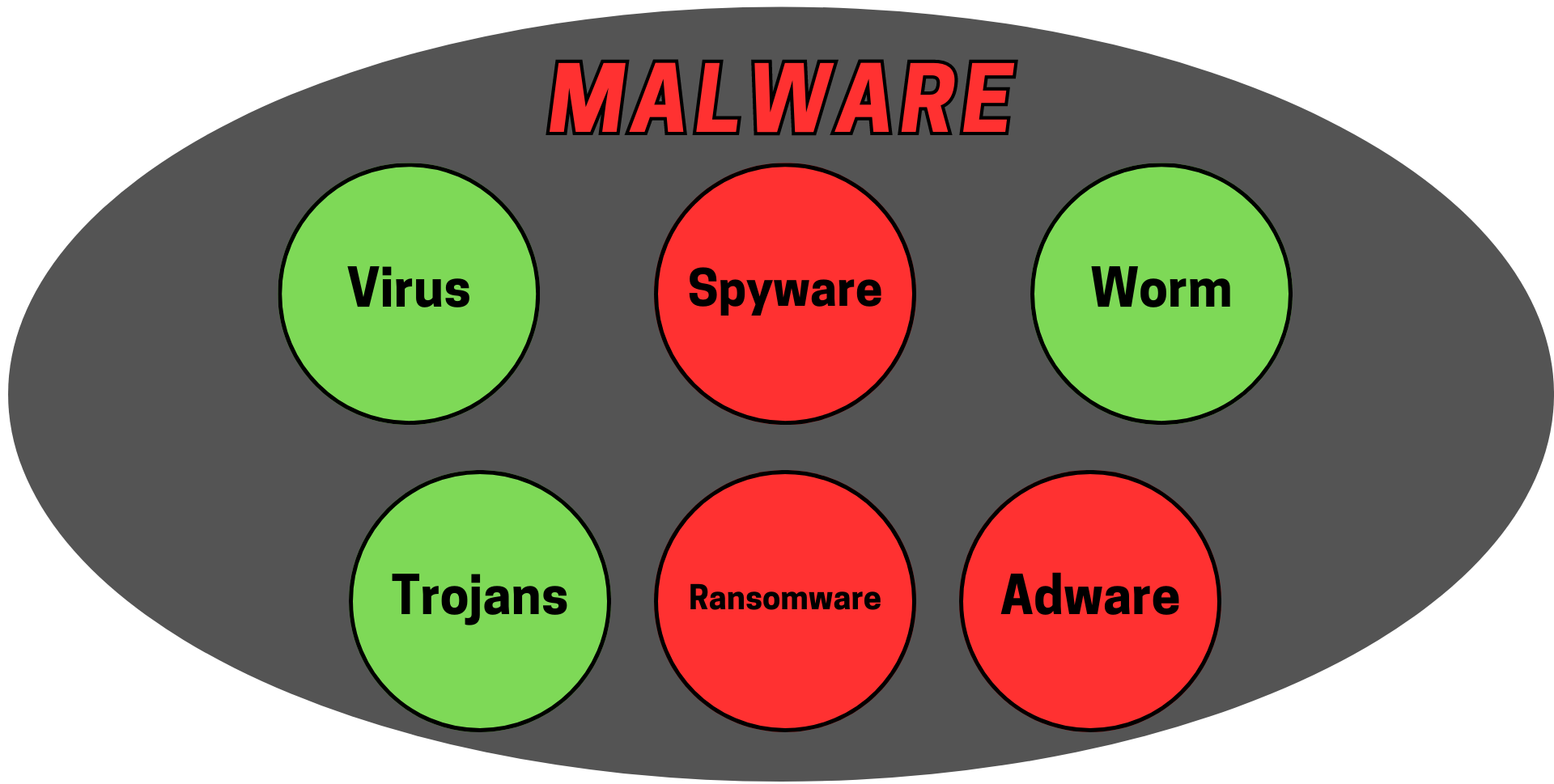
- Viruses: Viruses are one of the most well-known types of malware. They attach themselves to legitimate programs or files and infect other files upon execution. Viruses can spread rapidly, infecting an entire system or network, and may cause various issues, from data corruption to system crashes.
- Trojans: Named after the ancient Greek myth, Trojans masquerade as harmless or useful software, enticing users to download or install them. Once inside the system, Trojans can create backdoors, steal sensitive information, or disrupt computer operations. Unlike viruses, Trojans do not self-replicate.
- Ransomware: Ransomware is a particularly malicious form of malware that encrypts the victim's data, rendering it inaccessible until a ransom is paid to the attackers. This type of malware can cause devastating consequences for individuals and businesses alike.
- Worms: Worms are standalone malware that can spread across systems or networks without any human interaction. They exploit security vulnerabilities to replicate and distribute copies of themselves to other computers. Worms can cause significant network congestion and overload.
- Spyware: Spyware is designed to secretly gather sensitive information, such as passwords, browsing habits, or personal data, and transmit it to the attackers. It operates stealthily, often without the user's knowledge or consent.
- Adware: Adware is a type of malware that displays intrusive advertisements on infected devices. While not as harmful as other malware, adware can be incredibly annoying and disrupt the user experience.
- Keyloggers: Keyloggers track and record keystrokes on a device, allowing cybercriminals to steal sensitive information, such as login credentials and credit card details.
- Rootkits: Rootkits are sophisticated malware that grants unauthorized access to a system while remaining hidden from detection. They often target the core components (the "root") of an operating system to gain control.
- Botnets: Botnets are networks of compromised computers controlled by a single entity, the "bot herder." These infected computers, known as bots, can be used to carry out coordinated attacks, send spam, or conduct distributed denial-of-service (DDoS) attacks.
How Does Malware Spread?
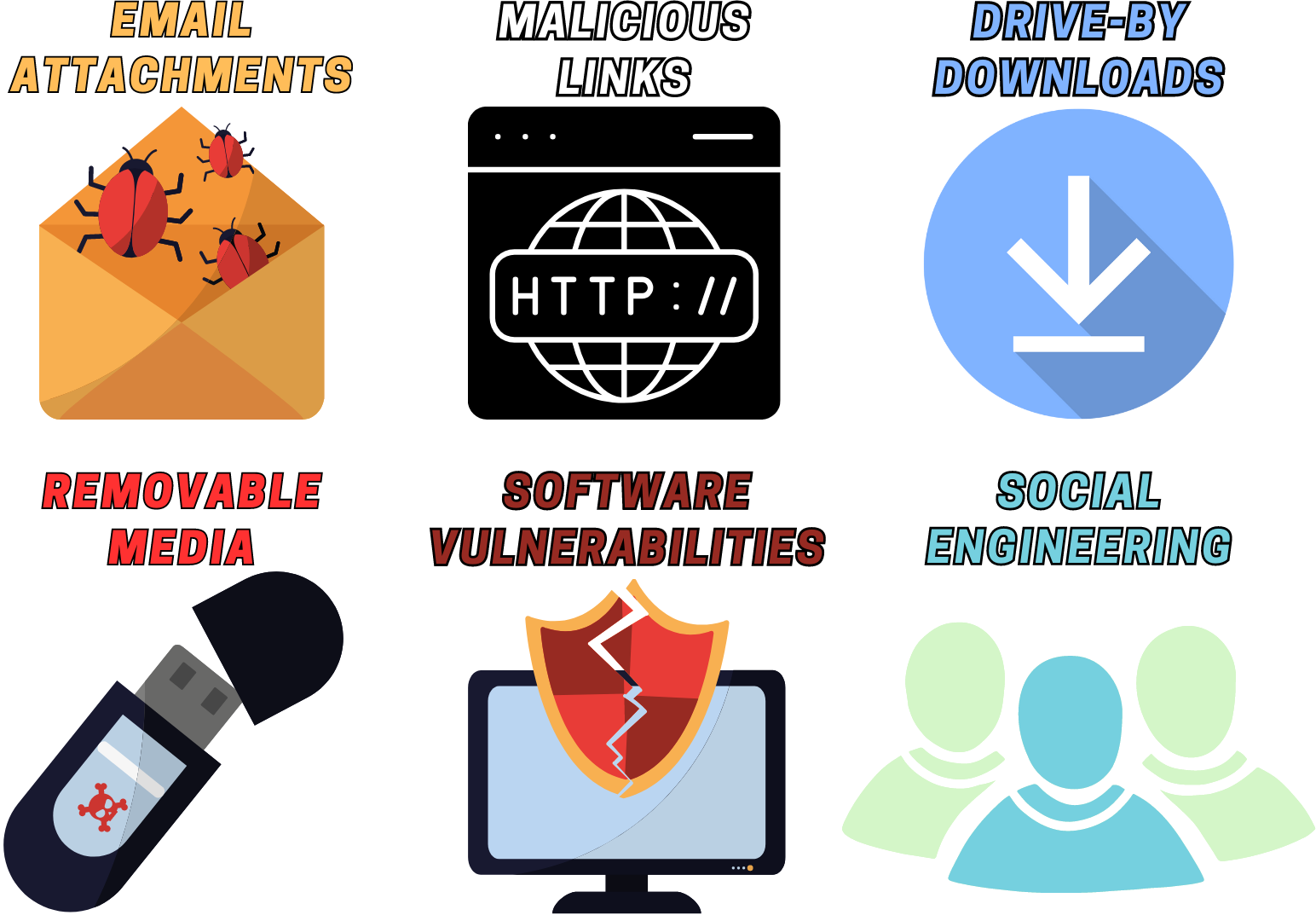
Malware can spread through various vectors, including:
- Email Attachments: Infected email attachments can exploit vulnerabilities in software or trick users into executing malicious code.
- Malicious Links: Hyperlinks leading to malicious websites or infected downloads.
- Drive-by Downloads: Malware can be automatically downloaded without the user's knowledge while visiting compromised websites.
- Infected Removable Media: USB drives or external storage devices can carry malware from one computer to another.
- Software Vulnerabilities: Exploiting security flaws in software or operating systems to gain unauthorized access.
- Social Engineering: Manipulating users into downloading or executing malware through deception.
Protect Against Malware
Preventing malware infections requires a proactive approach. Consider implementing these best practices:
- Keep Software Updated: Regularly update your operating system, software applications, and antivirus programs to patch known vulnerabilities.
- Use Strong Passwords: Employ strong and unique passwords for all accounts and change them regularly.
- Be Cautious with Email: Avoid opening suspicious email attachments or clicking on unknown links.
- Download from Trusted Sources: Only download software from reputable sources to minimize the risk of downloading infected files.
- Install a Reliable Antivirus Program: Invest in a reputable antivirus and anti-malware software to detect and eliminate threats.
- Backup Your Data: Regularly backup your important files to an external source to mitigate the impact of ransomware attacks.
- Enable Firewall Protection: Activate your system's firewall to block unauthorized access to your network.